The latest HP Wolf Security report points to AI being used to create malware scripts, threat actors relying on malvertising to spread rogue PDF tools, and malware embedded in image files.
The latest HP Wolf Security report points to AI being used to create malware scripts, threat actors relying on malvertising to spread rogue PDF tools, and malware embedded in image files.
At HP Imagine, HP Inc. issued its latest Threat Insights Report revealing how attackers are using generative AI to help write malicious code. HP’s threat research team found a large and refined ChromeLoader campaign spread through malvertising that leads to professional-looking rogue PDF tools, and identified cybercriminals embedding malicious code in SVG images.
The report provides an analysis of real-world cyberattacks, helping organisations to keep up with the latest techniques cybercriminals are using to evade detection and breach PCs in the fast-changing cybercrime landscape. Based on data from millions of endpoints running HP Wolf Security, notable campaigns identified by HP threat researchers include:
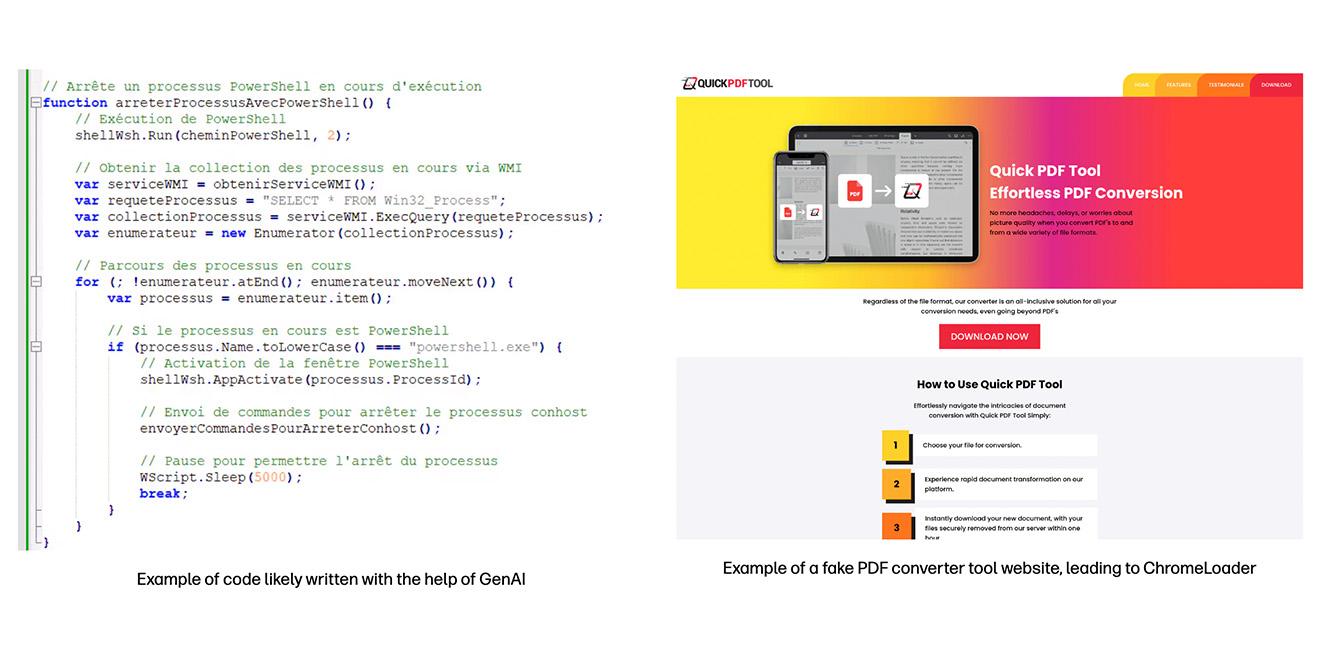
- Generative AI assisting malware development in the wild: Cybercriminals are already using GenAI to create convincing phishing lures but to date there has been limited evidence of threat actors using GenAI tools to write code. The team identified a campaign targeting French-speakers using VBScript and JavaScript believed to have been written with the help of GenAI. The structure of the scripts, comments explaining each line of code, and the choice of native language function names and variables are strong indications that the threat actor used GenAI to create the malware. The attack infects users with the freely available AsyncRAT malware, an easy-to-obtain infostealer which can record victim’s screens and keystrokes. The activity shows how GenAI is lowering the bar for cybercriminals to infect endpoints.
- Slick malvertising campaigns leading to rogue-but-functional PDF tools: ChromeLoader campaigns are becoming bigger and increasingly polished, relying on malvertising around popular search keywords to direct victims to well-designed websites offering functional tools like PDF readers and converters. These working applications hide malicious code in a MSI file, while valid code-signing certificates bypass Windows security policies and user warnings, increasing the chance of infection. Installing these fake applications allows attackers to take over the victim’s browsers and redirect searches to attacker-controlled sites.
- This logo is a no-go – hiding malware in Scalable Vector Graphics (SVG) images: some cybercriminals are bucking the trend by shifting from HTML files to vector images for smuggling malware. Vector images, widely used in graphic design, commonly use the XML-based SVG format. As SVGs open automatically in browsers, any embedded JavaScript code is executed as the image is viewed. While victims think they’re viewing an image, they are interacting with a complex file format that leads to multiple types of infostealer malware being installed.
Patrick Schläpfer, Principal Threat Researcher in the HP Security Lab, commented: “Speculation about AI being used by attackers is rife, but evidence has been scarce, so this finding is significant. Typically, attackers like to obscure their intentions to avoid revealing their methods, so this behaviour indicates an AI assistant was used to help write their code. Such capabilities further lower the barrier to entry for threat actors, allowing novices without coding skills to write scripts, develop infection chains, and launch more damaging attacks.”
By isolating threats that have evaded detection tools on PCs – but still allowing malware to detonate safely – HP Wolf Security has specific insight into the latest techniques used by cybercriminals. To date, HP Wolf Security customers have clicked on over 40 billion email attachments, web pages, and downloaded files with no reported breaches.
The report, which examines data from calendar Q2 2024, details how cybercriminals continue to diversify attack methods to bypass security policies and detection tools, such as:
- At least 12% of email threats identified by HP Sure Click bypassed one or more email gateway scanners, the same as the previous quarter.
- The top threat vectors were email attachments (61%), downloads from browsers (18%) and other infection vectors, such as removable storage – like USB thumb drives and file shares (21%).
- Archives were the most popular malware delivery type (39%), 26% of which were ZIP files.
Dr. Ian Pratt, Global Head of Security for Personal Systems at HP Inc., commented: “Threat actors are constantly updating their methods, whether it’s using AI to enhance attacks, or creating functioning-but-malicious tools to bypass detection. So, businesses must build resilience, closing off as many common attack routes possible. Adopting a defence-in-depth strategy — including isolating high-risk activities like opening email attachments or web downloads — helps to minimise the attack surface and neutralise the risk of infection.”